Sponsored by CSEMReviewed by Maria OsipovaMar 27 2023
The advent of Industry 4.0 has brought about the ability to gather, transmit, and utilize valuable data within specialized machinery systems, offering a range of advanced capabilities.
Despite these advancements, the sharing of data is viewed as a potential threat to intellectual property. To address this concern, CSEM has integrated its technologies into a secure, end-to-end framework that includes efficient data distribution and private computing.
This framework is expected to foster a more trustworthy environment for data sharing in the complex landscape of Industry 4.0.
Industry 4.0 has brought about a transformation in the manufacturing of specialized machinery. With the integration of real-time data acquisition and visualization capabilities, intelligence, and communication to enhance their products.
This unlocks new opportunities such as predictive maintenance, remote monitoring, remote reconfiguration, and advanced quality control. These smart systems often rely on Artificial Intelligence methods, which require large amounts of data for algorithm training.
The sharing of data among various actors in the industrial sector creates a complex trust environment, with concerns about potential risks to intellectual property and security. The recent increase in cyberattacks highlights the importance of securing production systems.
To ensure data confidentiality, authenticity, and appropriate access control, while maintaining the efficiency and functionality of the machinery and minimizing downtime, CSEM focuses on vertically integrated production lines. The organization's mission is to support innovation in Industry 4.0.
A production line is composed of a diverse combination of hardware and software components, often integrated into an ecosystem that includes data storage, advanced visualization, Decision Support Systems, and Enterprise Resource Planning systems. To ensure optimal performance, this system requires real-time data feed, such as that provided by CSEM's VISARD system.1
The data collected by the components of a machine has the potential to generate greater value for all stakeholders, including the component manufacturer, production line integrator, and machine owner.
However, machine owners are often reluctant to share production data due to fears of intellectual property or know-how leakage through cloud infrastructure.
To address this concern, CSEM has developed a solution for secure and private multi-actor data sharing while also providing high real-time data accessibility (Figure 1). The system is centered around CSEM's secure data distribution technology (XEMWAY), originally developed for use in the medical and IoT industries.
The solution ensures timely delivery of relevant data to the appropriate recipient, be it a data store, integrator's remote administration console, machine owner's remote monitoring interface, or the infrastructure of other parties.
An access control mechanism enables the data owner to manage permissions in a precise manner, ensuring that data is shared only among authorized and authenticated entities across the industrial floor.
This is achieved with the help of the end-to-end cutting-edge security framework,2 initially designed for medical applications, which enables the distribution of encrypted data across the ecosystem without sharing decryption keys. The data consumer can request the keys electronically, subject to the data owner's consent, at any level of granularity.
The key-sharing process is designed to be efficient and can safely disseminate sensitive encrypted data to multiple parties, such as data analysts. The encrypted data remains unusable unless an explicit request for the encryption key is issued and approved.
A CSEM technology based on Trusted Execution Environments allows a data analyst to decrypt, analyze, and destroy sensitive data within a secure environment, which only yields the results of the analysis, and keeps the raw data unavailable to anyone, including the analyst and the cloud service provider.
The solution is scalable and can leverage established commercial cloud services.
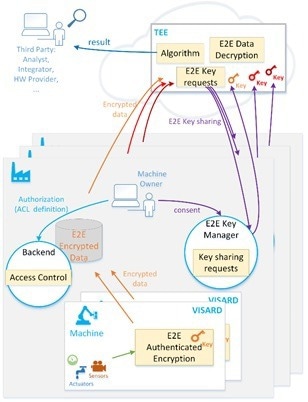
Figure 1. End-to-end secure and private, multi-actor data sharing. Image Credit: CSEM
The usefulness of the solution in unlocking new value and overcoming the issues of trust in the ecosystem is best illustrated by the use case of support and predictive maintenance.
The integrator is capable of handling a higher volume of data from multiple installations and can also seek assistance from the hardware providers.
This can be done by providing specific encrypted data sets to the providers, who would be granted the decryption keys based on their intended use. This enables the providers to receive valuable feedback.
Another pertinent application is algorithm training, where a developer trains a client's algorithm using data from various sources without risking data cross-leak. It is worth noting that the algorithm itself may also remain confidential to all parties involved.
References
- "CSEM VISARD" www.visard.ch
- M. de Ree, D. Vizar, G. Mantas, J. Bastos, C. Kassapoglou-Faist, J. Rodriguez "A Key Management Framework to Secure IoMT-enabled Healthcare Systems", CAMAD52502.2021.9617796.

This information has been sourced, reviewed and adapted from materials provided by CSEM.
For more information on this source, please visit CSEM.